Virtual Private Networks (VPNs)
Recent technological advances in broadband and dial data access offer a more cost-effective solution for supporting large numbers of remote users, as well as unprecedented network scalability and flexibility. These technology advances have created virtual private networks (VPN) using public links. They can be used to provide mobile workers with remote access to the corporate network - at the price of a local call. As with any use of public networks, one sacrifices privacy for cost and availability. Except a VPN is a network tunnel created for data transmission between two or more authenticated parties. A secure VPN encrypts data before passing it through the network tunnel. This creates an encrypted "pipe" between the user and the access device ensuring data integrity/authenticity, and user privacy. Apart from providing connectivity for remote users, VPNs can also be used to interconnect servers and complete networks, creating entities known as Extranets.
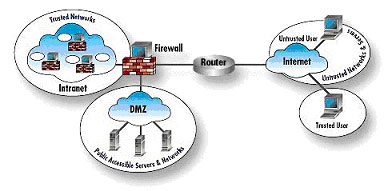
Virtual Private Networks can be implemented by using propitiatory systems from Cisco, NetScreen Intel, Nokia, Checkpoint, Lucent and others. Point to point VPNs can also be created using embedded protocols in Operating Systems like Windows, Linux and other Unix variants.
